Information security governance
Control environment
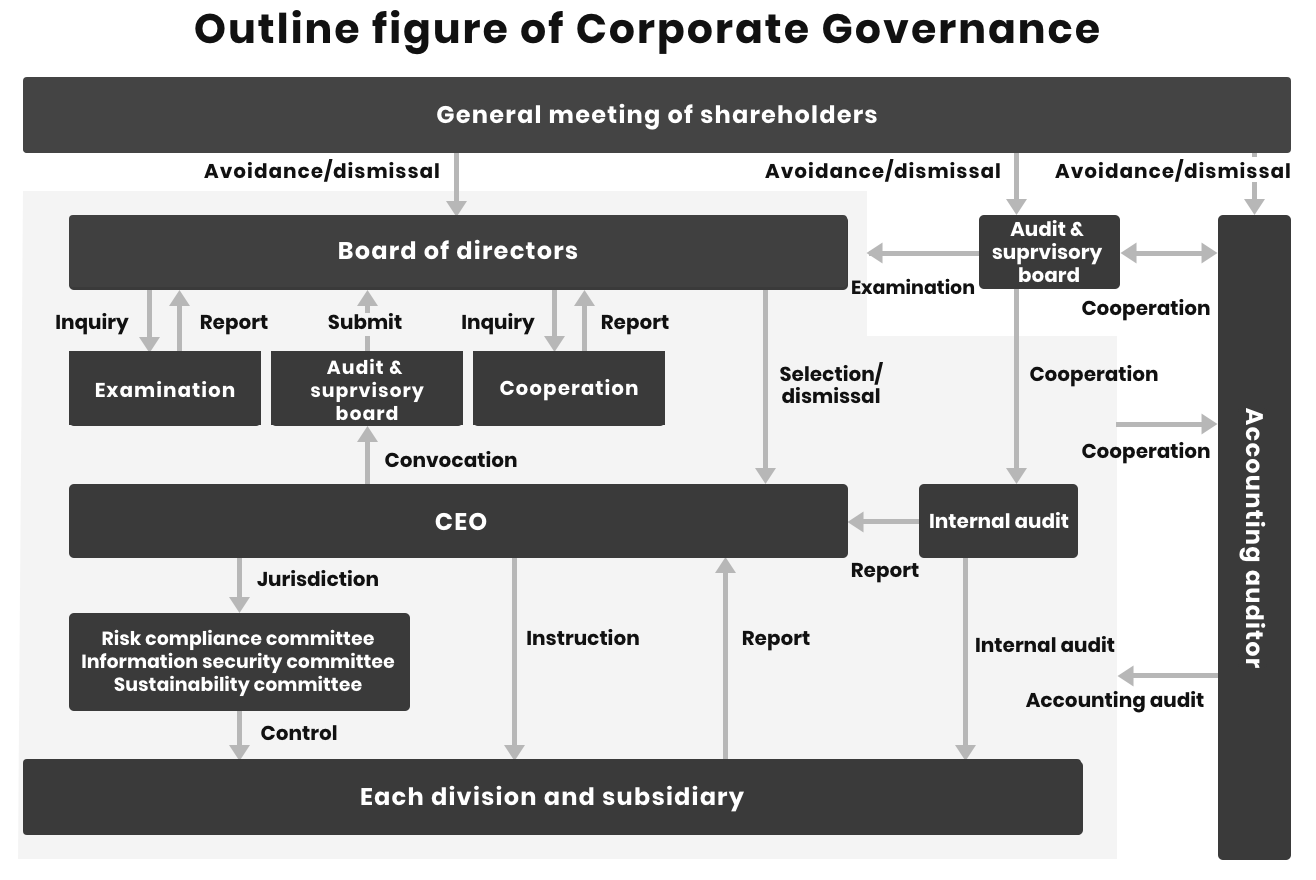
Outline of Corporate Governance and reasons for the adoption of the system
WingArc1st has adopted an Audit & Supervisory Board Member system and has established a Board of Directors, an Audit & Supervisory Board and an Accounting Auditor as statutory institutions. Additionally, the Company has also established Special Committees, a Nomination & Compensation
Committee, a Risk Compliance Committee, an Information Security Committee and a Sustainability Committee as arbitrary institutions.
The Company has adopted this system to ensure the transparency and soundness of its management and to expedite decision-making. Furthermore, to separate business execution functions and decision-making/supervisory functions, the Company establishes an executive officer system and the Nomination and Compensation Committee as an arbitrary institution to strengthen the supervisory functions on management.
Control activities
The Information Security Committee Regulations establishes the Information Security Committee as a subordinate organization of the Risk Compliance Committee in accordance to the Risk Management Basic Regulations. The Information Security Committee shall formulate basic policies concerning the management of information assets of WingArc1st and its group companies, carry out implementation procedures, evaluation, and analysis, and respond to incidents and accidents such as leakage of information assets, thereby ensuring the appropriate management and operation of the Company's information assets.
Information dissemination
Once a year, the management team holds a General Meeting of Employees and once a month, an Activity Sharing Meeting to explain management policies, status, and communicate instructions to all employees. Materials are posted on the company portal site and shared after the event for employees who were unable to attend. The company portal site also transmits messages from directors, notices regarding compliance, internal regulations, and important matters concerning shareholders, as appropriate.
If an information security incident occurs, it will be immediately reported to the Information Security Committee using the incident report procedure.
Information security training
The Company conducts information security training for new employees when they join the company. In addition, e-learning and other training programs are conducted once a year for all employees.
Monitoring
Internal audits and management reviews are conducted annually.
Risk assessment
The Company conducts risk assessments annually and when relevant events occur to identify, analyze, and evaluate risks.